Email Security Best Practices for Employees
Kalamazoo, MI | August 13, 2025
Believe it or not, 75% of cyberattacks start with an email.
That’s right—even with all the advancements in AI, old-fashioned emails are still the leading cause of security breaches. And when you think about it, that makes a lot of sense. Emails are home to the greatest cybersecurity risk of all: human error.
Simply put, it’s impossible to be vigilant 100% of the time. You may have perfect days, weeks, or even months, but as the years pass everyone will miss something. And hackers know this.
That’s the most important thing to remember—you have to be vigilant every time, but cybercriminals only have to get lucky once. And at an organizational scale, it only takes one slip-up from one employee to compromise an entire company.
So, is cybersecurity hopeless? Do we all just exist between the last hack and the next?
Luckily, no.
With the right cybersecurity approach, you can keep your business and your employees safe from email-based cyber attacks. Today, we’re sharing some best practices for email security at your organization.
Use Your Email Software’s Built-In Security
The minds behind email software such as Outlook know how dangerous fraudulent emails can be. That’s why they’ve created some great tools to help you filter them out.
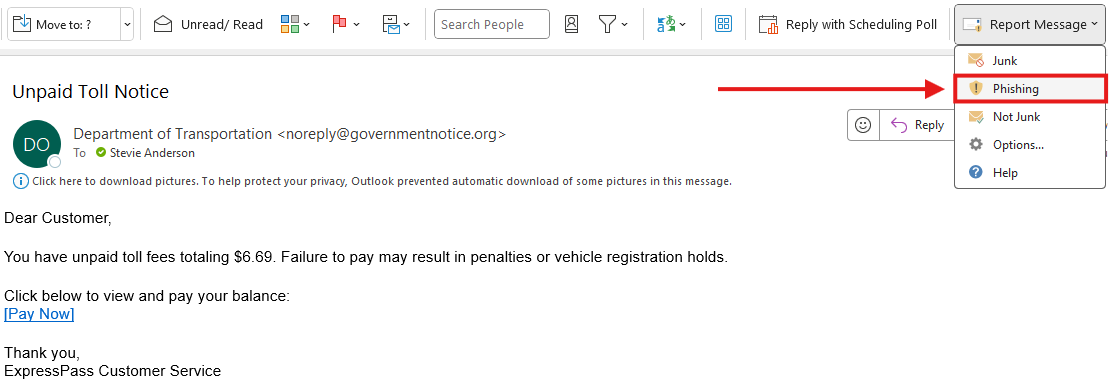
How to Report Phishing Attempts in Outlook
You probably already know that suspicious emails automatically get filtered into the “spam” or “junk” folder on your desktop. But do you know how Outlook decides which emails are suspicious? Well, it’s partially thanks to people just like you.
Email software like Outlook has a button for reporting phishing emails, and people use it all the time. When you report phishing emails in Outlook, they get sent straight to Microsoft for analysis. From there, Microsoft’s AI scans the email you reported and compares it to other, similar ones for common trends.
Here’s how you report phishing attempts in Outlook:
Open the email you want to report.
In the upper right corner, click the “Report Message” button.
Select “Phishing.”
It’s that easy!
From there, Outlook should move the suspicious email into your “Junk” folder. And depending on your organization’s email policy, all future emails from that sender may be flagged as suspicious.
Forward any phishing emails to the Anti-Phishing Working Group at reportphishing@apwg.org. Though it may seem small, the information you send can help protect people just like you from identity theft, financial theft, and ransomware.
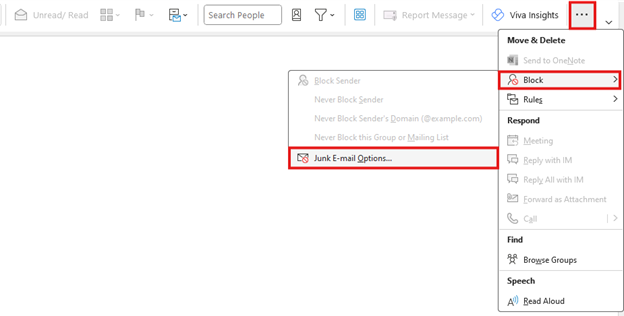
Setting Up Advanced Junk Email Options
You can change how carefully Outlook filters out junk and phishing emails. Here’s how:
Click on the three dots in the upper right corner of your Outlook screen.
Select “Block”
In the menu that opens, select “Junk E-Mail Options…”
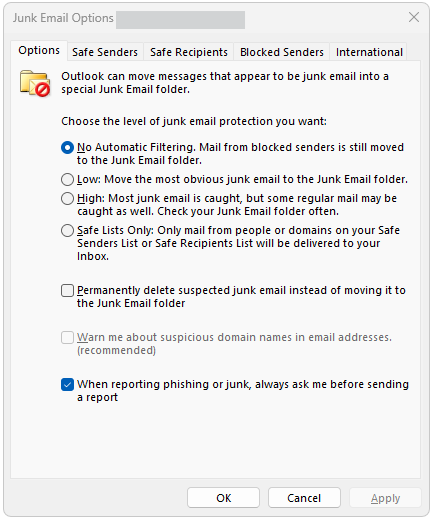
You’ll know you’re in the right place if a menu like titled “Junk Email Options” pops up.
In that box, you can choose the level of junk email protection you want. There are 4 levels:
No Automatic Filtering. This turns off automatic filtering, so nothing goes to your Junk email unless you move it there.
Low. This moves only the most obvious spam and phishing emails to your Junk folder.
High. “High” catches more junk and phishing emails than “Low,” but it can also catch regular emails by mistake.
Safe Lists Only. This is the strictest option. When selected, only emails from people and domains that you’ve designated as safe will reach your inbox.
There are also a few options you can enable to make your life easier:
Have Outlook permanently delete suspected junk emails instead of moving them to your “Junk” folder.
Have Outlook warn you about suspicious domain names in the emails you receive.
Have Outlook ask you before sending a junk or phishing report.
Limit Your Email Address Exposure
The best way to keep your email secure is by keeping it hidden from fraudsters.
Hackers love to scour social media and company websites, where your contact information is posted for the world to see. Once they have that information, there’s no putting the cat back in the bag.
Here’s a couple ways to keep your address hidden from people who want to send you phishing emails.
For SMBs: Use Contact Forms on Your Website, Not Email Links
If you have a company website, then think carefully before posting your or other employee emails. Instead, use a contact form.
Contact forms are a one-way street—personal information goes in, but it doesn’t come out. Anyone who wants to reach you still can, but they won’t be able to see your email unless you choose to follow up.
For Individuals: Use Different Emails for Different Purposes
It’s tempting to use one email for everything—but don’t do it. When you use only one email address instead of multiple, you open yourself up to two risks:
Increasing the chances that hackers find that email.
Putting all your essential information in one place for hackers to access.
Let me explain.
When you only have one email address, you’ll need to use it more often—it’s the only way people can reach you through email, after all. And the more you share your email, the more likely it is that your address gets leaked through someone else.
Just think of all the services you’ve subscribed to using your email. Ask yourself if you’ve used your email to sign up for any of the following services:
Facebook
LinkedIn
Twitter/X
eBay
Microsoft
All the corporations above have had millions of user emails leaked at least once (if not more).
To stay safe, I recommend using at least four different email accounts. That might sound like a lot, but trust me—it makes email management much easier.
I recommend a different email account for:
Work. Most people already keep a separate work email because it creates a boundary between the professional and personal. If you don’t already have one (like if you’re a newer small business owner), I recommend making one immediately.
Social Life. Instead of a catch-all personal email address, I recommend keeping one specifically for your social life. This is the email address that you give directly to other humans, such as friends and family.
Online Services. This is the email you use every time you have to make an account with an online service. By keeping an email specifically for subscription services, you make sure your other accounts aren’t at risk when a big corporation (inevitably) gets breached.
Financial & Legal. This will be your most secure email account, with your most complicated password and multi-factor authentication (MFA). I promise that keeping a separate email for financial and legal purposes will give you some peace of mind that your most sensitive information is secure.
As a final note, don’t send emails between these 4 different accounts. If one of them ever gets breached, you don’t want a hacker to have any information about your other accounts.
Wondering if your email has already been leaked online? You can actually check if your email has been exposed in a data breach at haveibeenpwned.com. As of August 2025, 14.99 billion accounts have been leaked worldwide — is yours one of them?
Conclusion: Every Little Bit Helps
Ultimately, it’s impossible to secure yourself from every threat out there. That said, you don’t need to be impenetrable—you just need to be more trouble than you’re worth.
Most hackers will move on when they realize that you take cybersecurity seriously. After all, hackers don’t want your information, they want easily accessible information. That’s why it’s important to make sure that everyone’s email accounts at your organization are secure.
For more information on managed security services for your SMB, click here to contact us today!